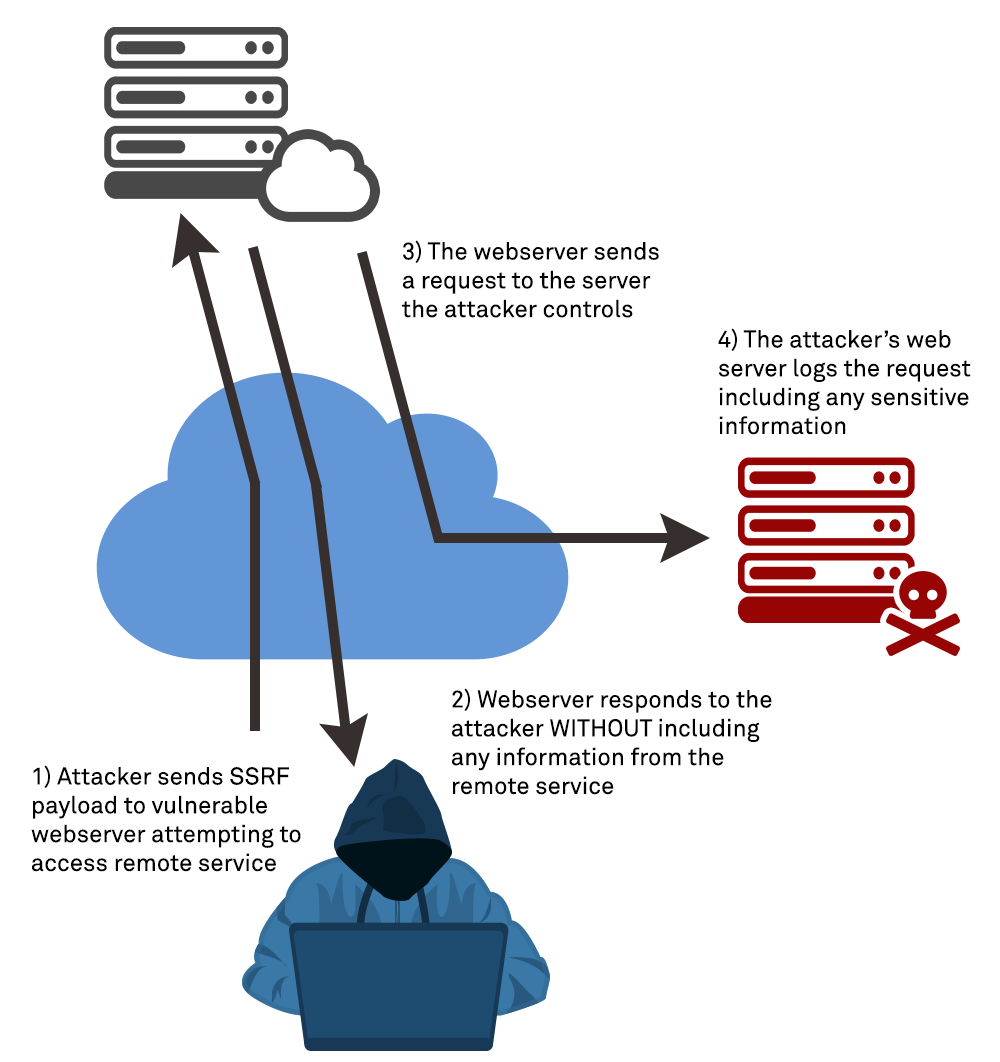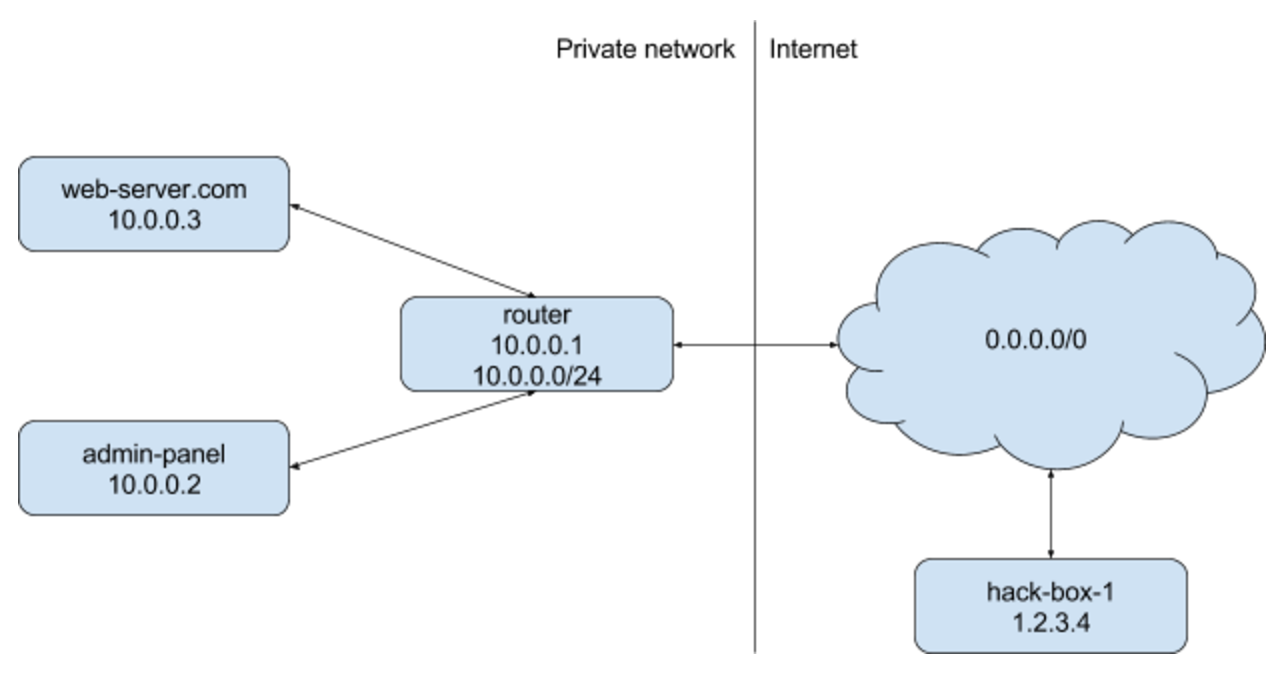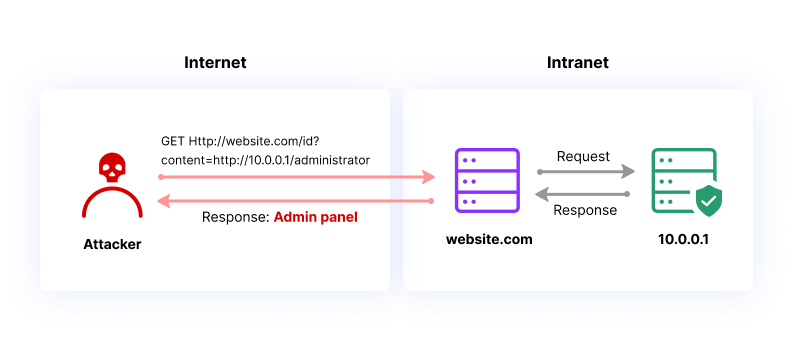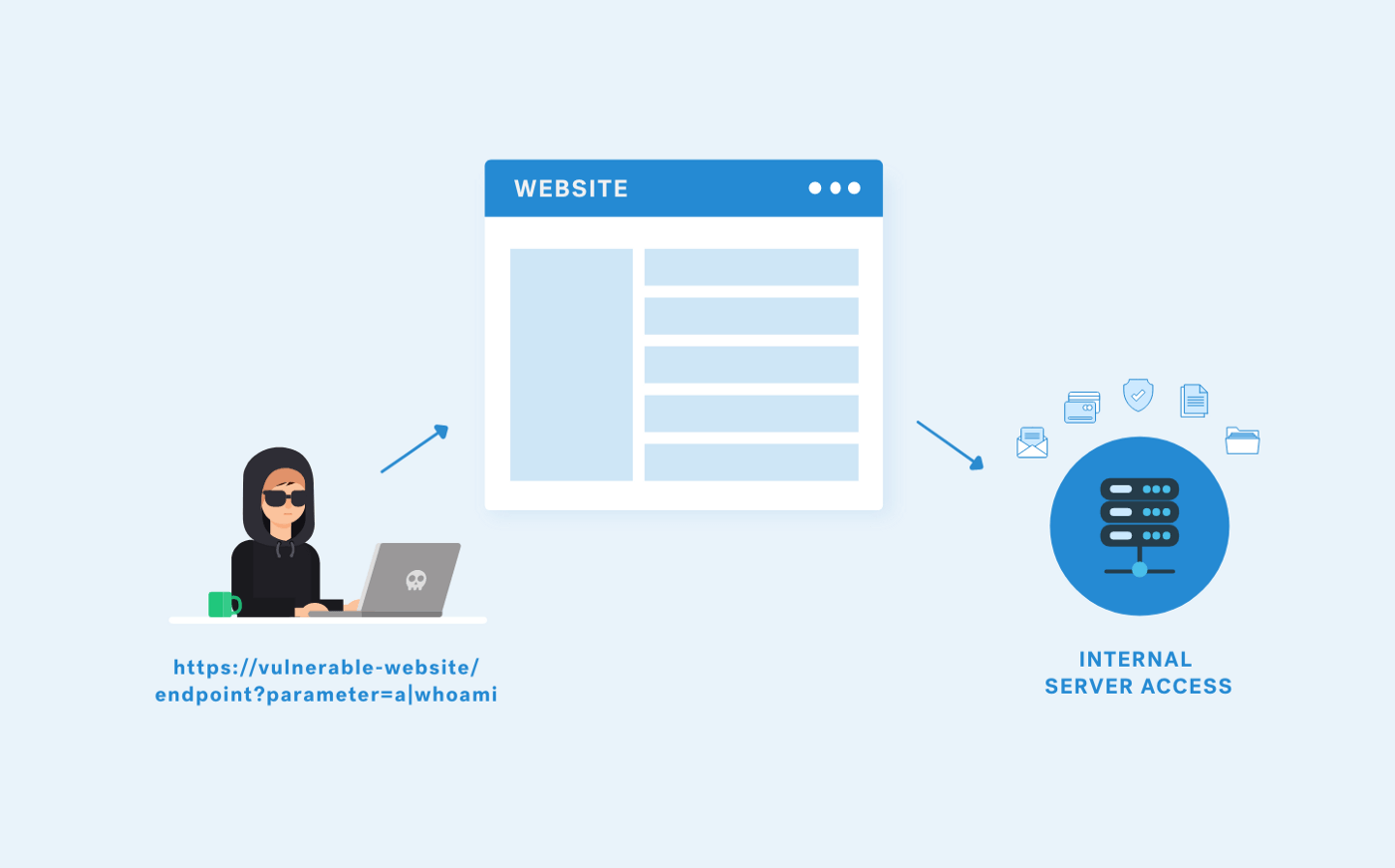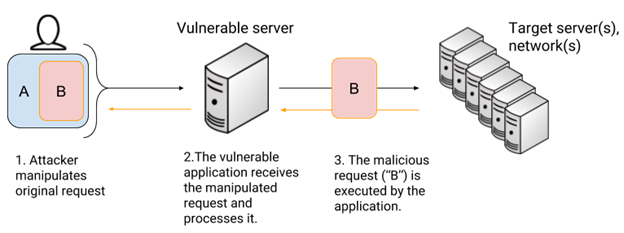
SSRF's up! Real World Server-Side Request Forgery (SSRF) Shorebreak Security - Experts in Information Security Testing
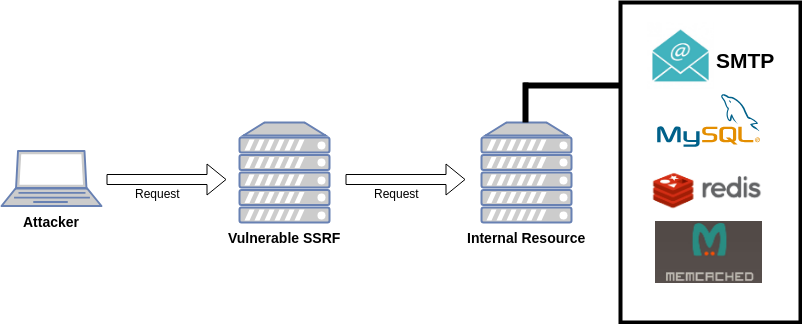
Beginner Guide To Exploit Server Side Request Forgery (SSRF) Vulnerability | by Muh. Fani Akbar | InfoSec Write-ups

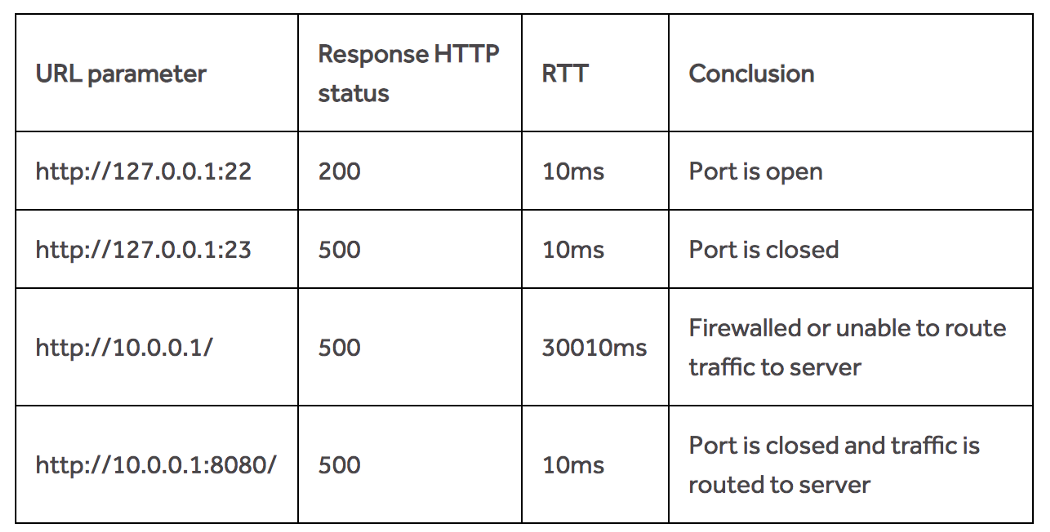
Using SSRF/XSPA to extract data from internal machines | Hands-On Application Penetration Testing with Burp Suite

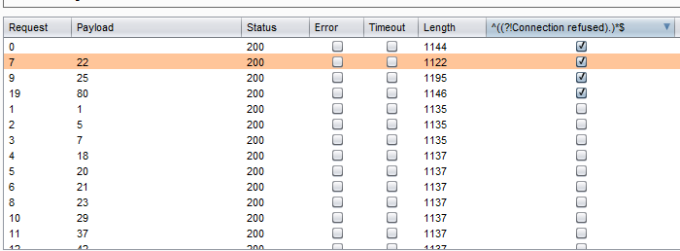
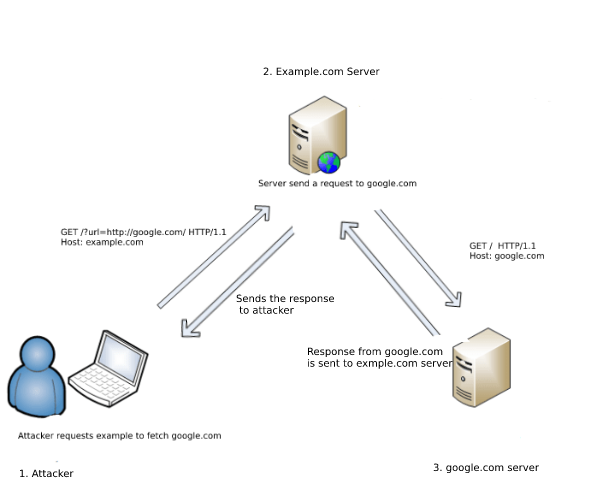
![Exploiting SSRF vulnerability [Server-Side Request Forgery] Exploiting SSRF vulnerability [Server-Side Request Forgery]](https://www.vaadata.com/blog/wp-content/uploads/2019/10/SSRFmap.png)