
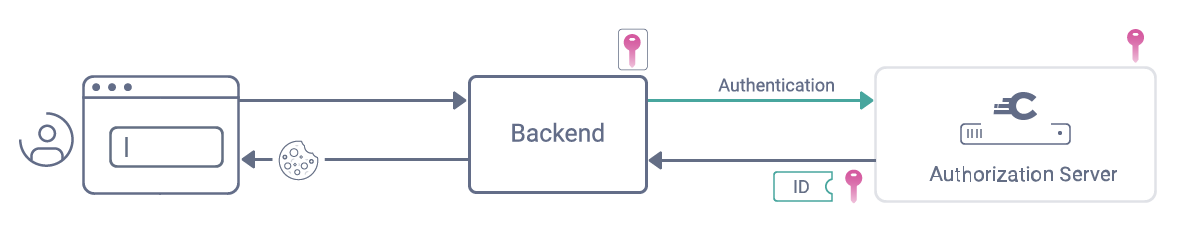
Debug Logging Microsoft.Identity.Client and the MSAL OAuth client credentials flow | Software Engineering
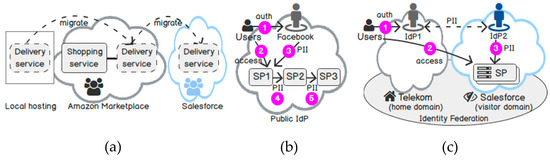
Future Internet | Free Full-Text | Identity-as-a-Service: An Adaptive Security Infrastructure and Privacy-Preserving User Identity for the Cloud Environment

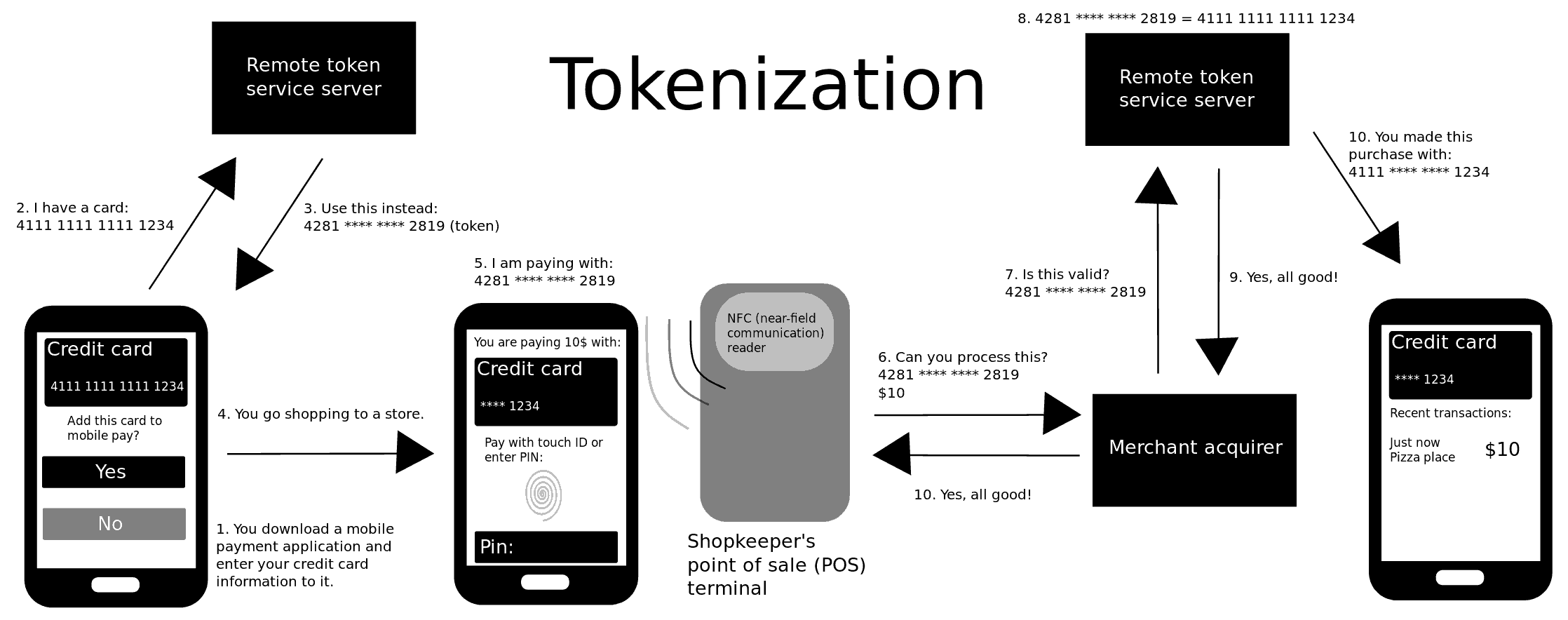
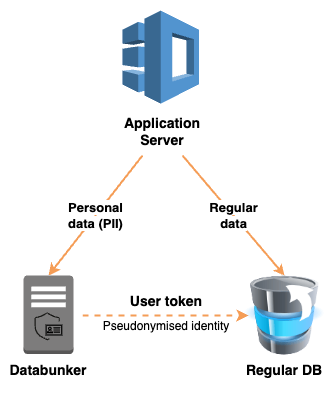
Towards A Tokenized Data World: A New World Is Being Created | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium





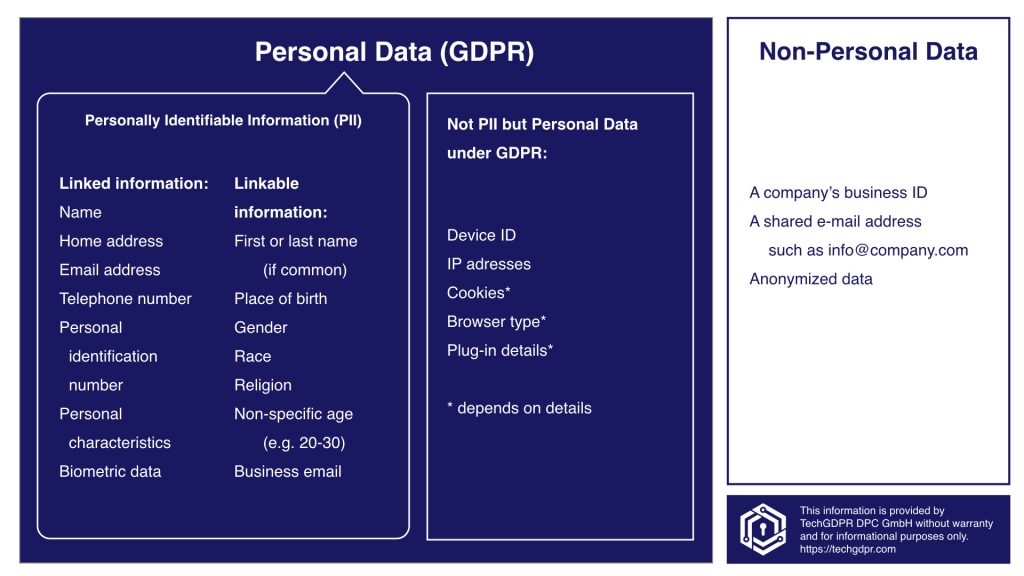
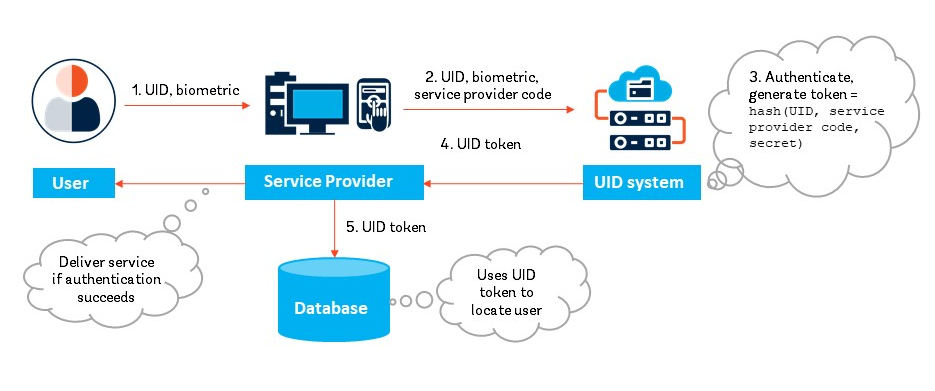



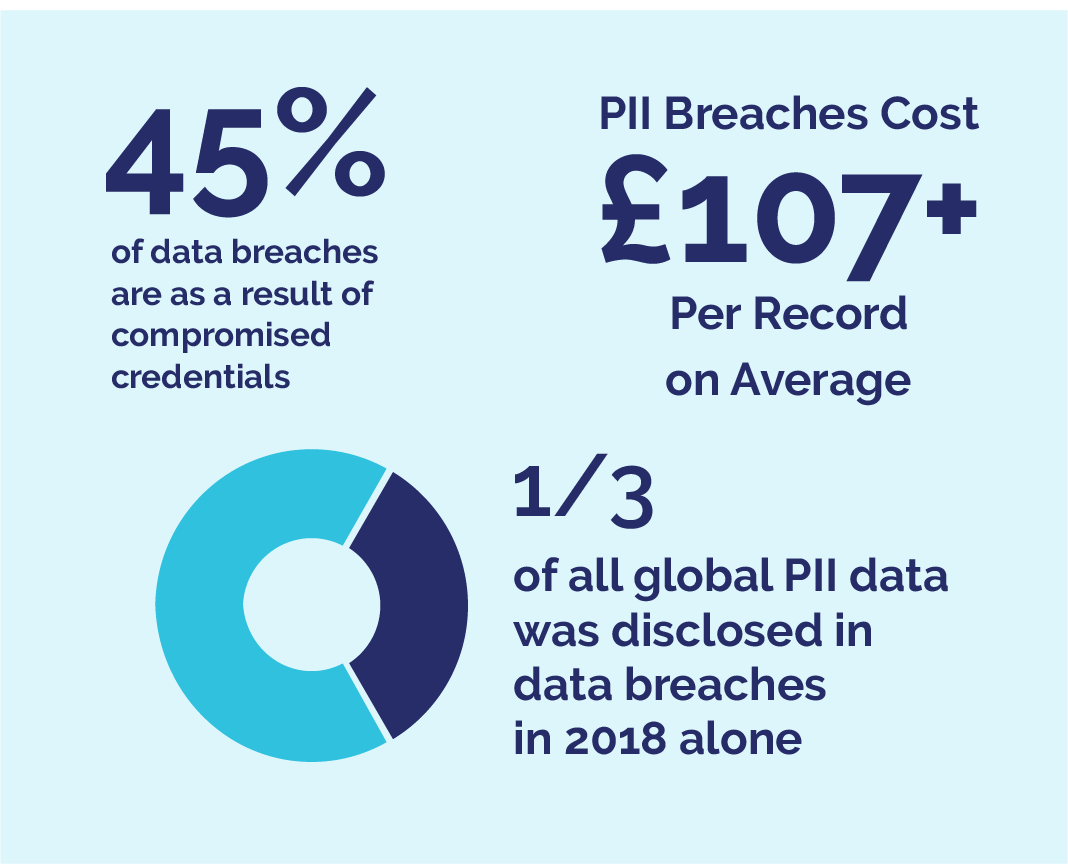

.jpeg)


